Cyber Threats #03 - Why it’s time to shift focus from mundane tasks to real threats?
New York Times source code stolen, Bypass In Veeam Backup, AWS unveils new and improved security features, Apple Private Cloud Compute and more...
Welcome to the third edition of the Cyber Threats Newsletter. The goal is to deliver weekly updates with the latest in cyber threats, to help accelerate innovation and collaboratively build a more secure future!
Why it’s time to shift focus from mundane tasks to real threats?
The daily day of cybersecurity teams often contrasts with the exciting image of finding advanced adversaries. Many times, their days are consumed with tasks that add little value and lead to burn-out and waste resources from real threat detection and response.
The reality is that, although teams need to prepare for high-profile incidents and APTs, most of their work is not directly related to these or gets lost among many tools with little focus.
To improve this situation, it's crucial to develop tools and strategies that automate routine tasks, optimize workflows and are driven by data, freeing up teams to focus on what really matters: proactive detection and rapid response to threats.
For example, starting with ensuring that the entire team understands the top threats their company (or clients) faces. From there, they can explore how these can be exploited, for example, using the MITRE ATT&CK framework. KPIs should measure not only Mean Time to Response (MTTR) but also the coverage level over the defined top threats.
Solutions, whether in-house or commercial, should be easy to use and maintain, and should seamlessly integrate with the daily operations of security teams and data systems (like date warehouses), ultimately empowering security analysts to focus on what's important.
Because one important thing to understand is that attackers only need to find one weak point to exploit!
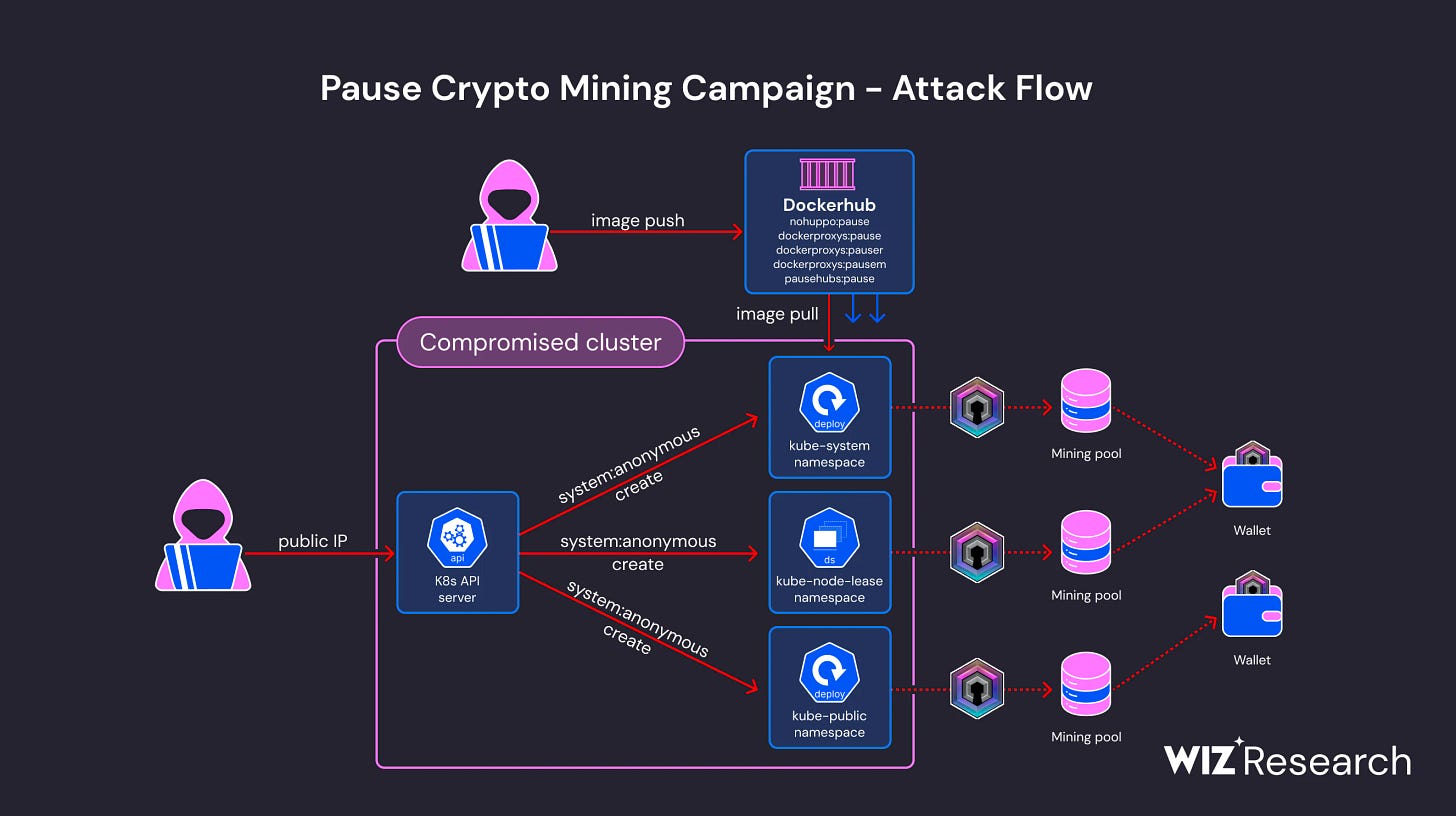
Years ago, while I was in the SOC of a national cybersecurity agency, we detected a Monero miner exploiting a Java remote code execution vulnerability. Many years later, I read this article where machines running Kubernetes are now being used to mine DERO (the initial access vector is an externally accessible Kubernetes API server with anonymous authentication enabled [T1190]), and I think, if after so many years we continue with the same types of attacks without being able to react in time, it's clear that we must seek continuous processes that proactively search for cyberattacks and respond to them in real time, moving away from traditional security solutions that react only once known threats have been identified.
Now you might be asking… how? The reality is that it’s not easy, but I suggest starting by rethinking Level 1 with a threat-driven mindset!
Week in review
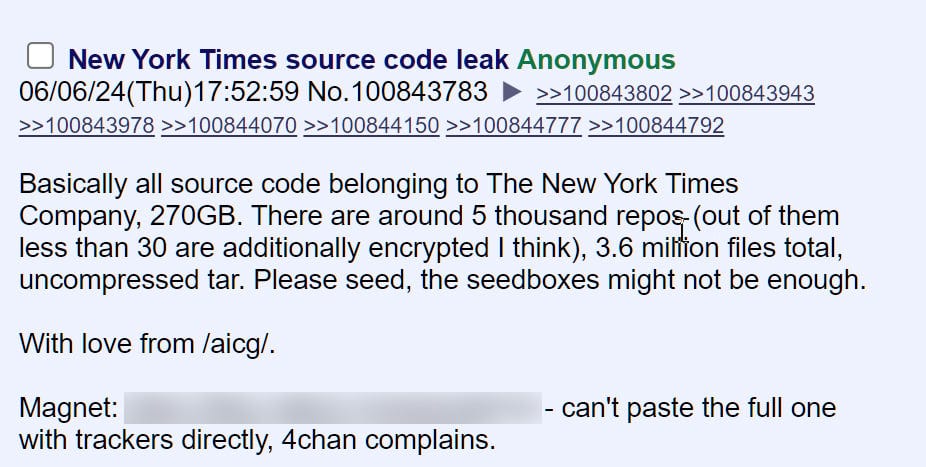
New York Times source code stolen using exposed GitHub token
Internal source code and data belonging to The New York Times was leaked on the 4chan message board after being stolen from the company's GitHub repositories in January 2024, The Times confirmed to BleepingComputer.
As first seen by VX-Underground, the internal data was leaked on Thursday by an anonymous user who posted a torrent to a 273GB archive containing the stolen data.
A Critical Auth Bypass In Veeam Backup Enterprise Manager (CVE-2024-29849)
The exploit targets Veeam’s API by sending a specially crafted VMware single-sign-on (SSO) token to a vulnerable service. Then a server under the control of the attack responds positively to the validation, granting the attacker administrator access.
Users of JetBrains IDEs at risk of GitHub access token compromise (CVE-2024-37051)
JetBrains has fixed a critical vulnerability (CVE-2024-37051) that could expose users of its integrated development environments (IDEs) to GitHub access token compromise.
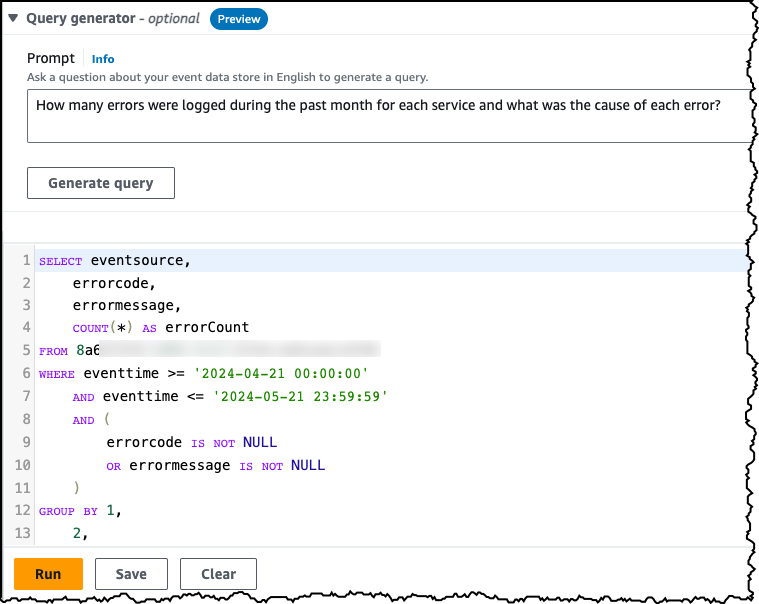
AWS unveils new and improved security features
At its annual re:Inforce conference, Amazon Web Services (AWS) has announced new and enhanced security features and tools. Like simplify AWS CloudTrail log analysis with natural language query generation in CloudTrail Lake.
Interesting Interviews, Tools and More
Apple Private Cloud Compute: A new frontier for AI privacy in the cloud
Apple created Private Cloud Compute (PCC), a groundbreaking cloud intelligence system designed specifically for private AI processing. For the first time ever, Private Cloud Compute extends the industry-leading security and privacy of Apple devices into the cloud, making sure that personal user data sent to PCC isn’t accessible to anyone other than the user — not even to Apple.
YetiHunter: Open-source threat hunting tool for Snowflake environments
A threat detection and hunting tool companies can use to query their Snowflake environments for evidence of compromise.
Emulate APTs lab
Solve emulated APT-level incidents in a lab environment from reconnaissance to exfiltration. These technical labs are designed to test your incident response abilities against APT-level threats.
MalSearch: Malware Source Code Search Engine
A dedicated place to Search, Bookmark, Copy and Download all Malware source code and projects available on the internet. By https://twitter.com/_Ghast1y
Thanks for reading. If you want to be up to date with the last threats and news in the cybersecurity world, subscribe!