Cyber Threats #01 - Snowflake, Check Point PoC, GPT-4o Vision for Threat Intel, and more...
Welcome to the first edition of the Threat Intelligence Newsletter!
Welcome to the first edition of the Threat Intelligence Newsletter. The goal is to deliver weekly updates with the latest in threat intelligence and cybersecurity related, to help accelerate innovation and collaboratively build a more secure future!
Week in review
Snowflake breach is behind Ticketmaster and Santander
It appears the cause of these breaches are client accounts with weak or compromised passwords match with a lack of Multi-Factor Authentication enabled. Santander released a statement noting that they “recently became aware of an unauthorized access to a Santander database hosted by a third-party provider.” CISA has added this vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
Breach: Dell API abused to steal 49 million records
A threat actor known as Menelik abused a partner portal API to scrape the information of approximately 49 million Dell customer records. The stolen data included customer names, order numbers, service tags, installed locations, and more.
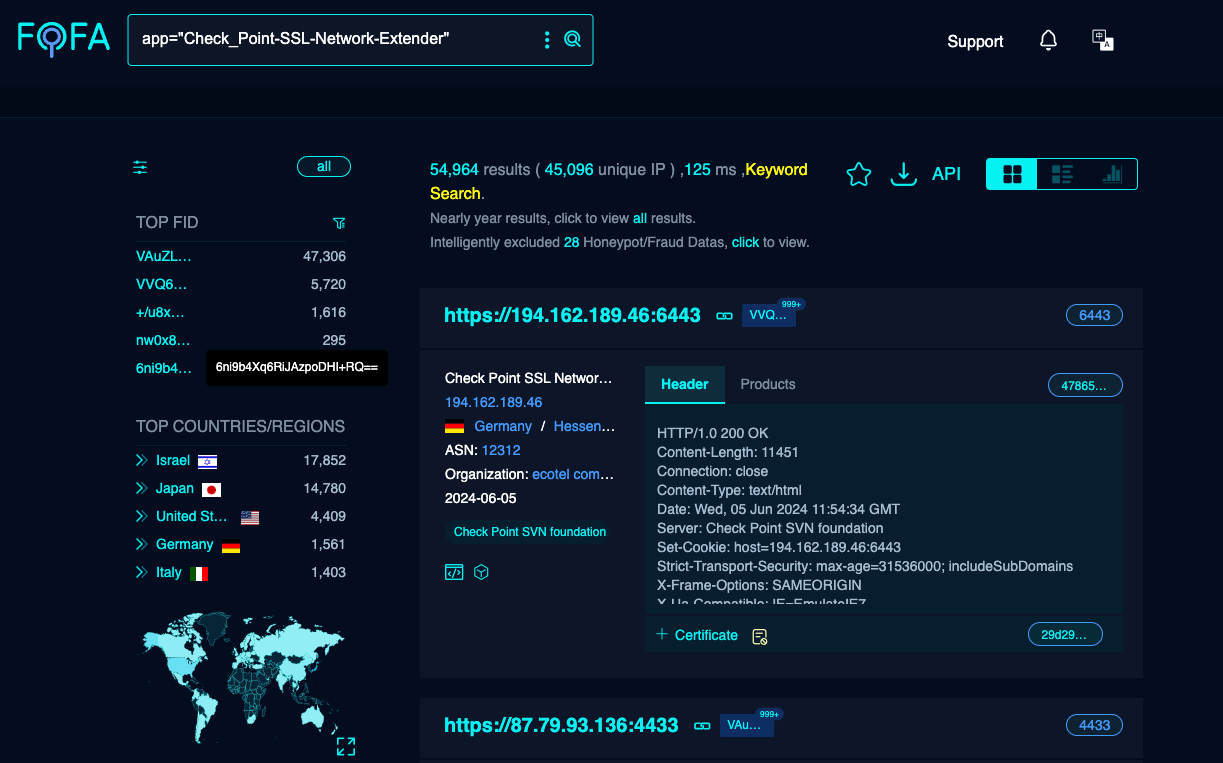
PoC for Check Point Vulnerability Released
Active exploitation of this vulnerability has been observed in the wild by multiple threat actors. A PoC was publicly released on May 30, 2024. The vuln is tracked as CVE-2024-24919 and could allow an unauthenticated remote attacker to read local files from the affected Security Gateway, including any exposed sensitive files such as password data, SSH keys, or other credentials.
A fast search in Fofa returns more than 45k unique IPs:
Fofa Dork:
app="Check_Point-SSL-Network-Extender"Shodan Dork:
"Server: Check Point SVN" "X-UA-Compatible: IE=EmulateIE7"Ideas Corner
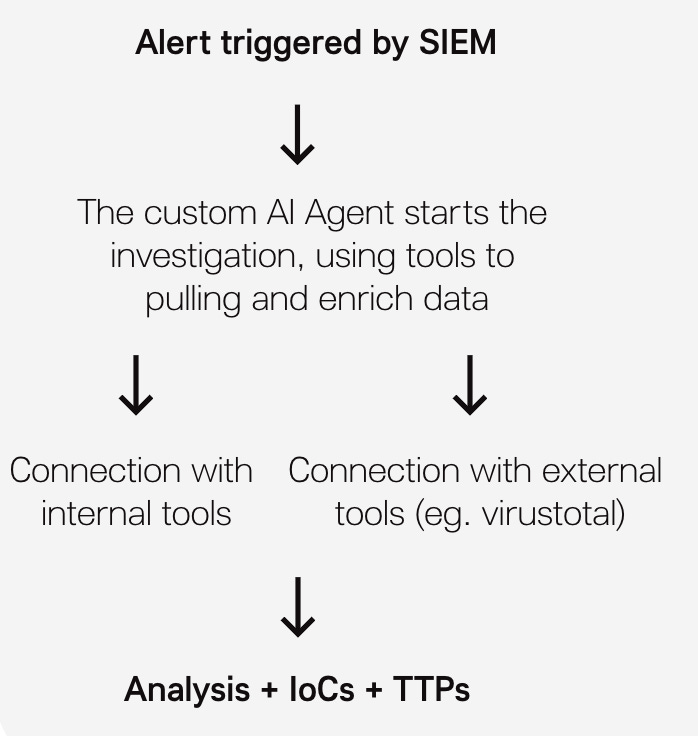
Leveraging LLMs for Threat Intelligence
Integrating AI into everything has become incredibly popular these days, but the question I always have in mind is how can we use the power of GenAI to enhance Threat Intelligence or SOC efficiency, reduce response times, and focus on what's important?
This example “Time Series Analysis by Leveraging GPT-4o Vision for Threat Intel” or this other “Our TRAM Large Language Model Automates TTP Identification in CTI Reports“ can be an answer.
One significant challenge is alert triage, burdened by alert overload and the rapid increase in cyberattacks. Why not reduce manual tasks with an efficient workflow?
Of course GenAI is not magic. Monitoring responses, refining prompts, and improving data are crucial steps in leveraging this technology effectively.
Interesting Interviews, Tools and More
The Gentlemen Hackers interview: The Grugq
Many years ago that I listen the talk OPSEC: Because Jail is for wuftpd from The Grugq, and now in this intersting interview they discuss the evolution of hacking, the human aspect of hacking operations, and some skepticism towards the discovery of a potential security breach involving a half-second delay in SSH communications.
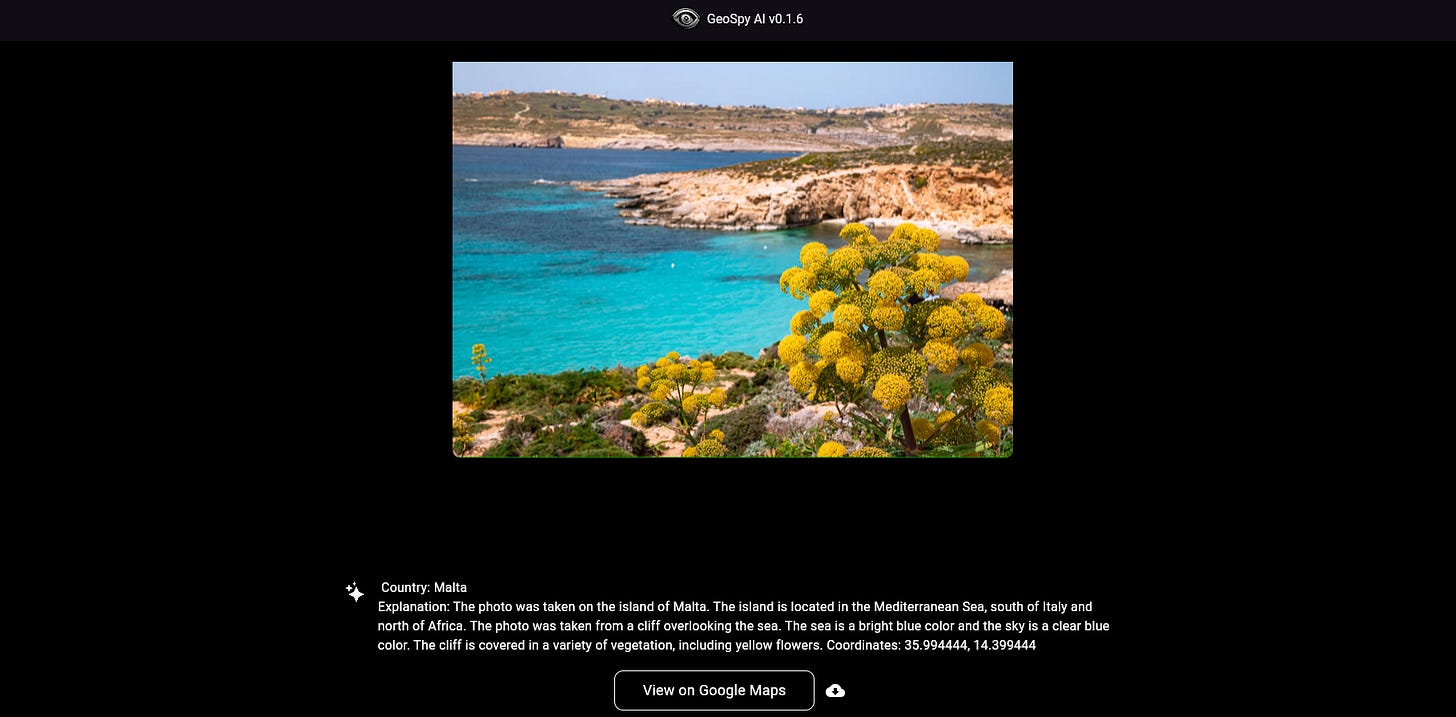
Geospy.ai: Photo location prediction using AI
Talking about OPSEC… I came across this tool Geospy.ai in twitter, and is really good. GeoSpy is a cutting-edge AI platform specialized in geo-estimation and location prediction, leveraging pixel data to accurately infer geographical locations
Sherlockeye.io OSINT tool
Sherlockeye is a tool designed to elevate your research and analysis (on emails). By the combined power of leading search engines like Google and DuckDuckGo, alongside cutting-edge AI language models, Sherlockeye delivers unmatched insights and understanding from your data.
API Security Best Practices
This post explains how APIs are the backbone of modern applications. They expose a very large surface area for attacks, increasing the risk of security vulnerabilities. Common threats include SQL injection, cross-site scripting, and distributed denial of service (DDoS) attacks.
Thanks for reading. If you want to be up to date with the last threats and news in the cybersecurity world, subscribe!